We regularly update all of our dependencies via dependabot, Renovate, or our own automation on RWX to open PRs.
Quickly adopting security and bug fixes is a good engineering practice. It's also helpful to identify potential issues with upgrades as soon as possible.
#Noticing a Character Encoding Issue
Last August, we noticed an encoding issue in our logs. Note the funky question mark characters towards the bottom of the logs.
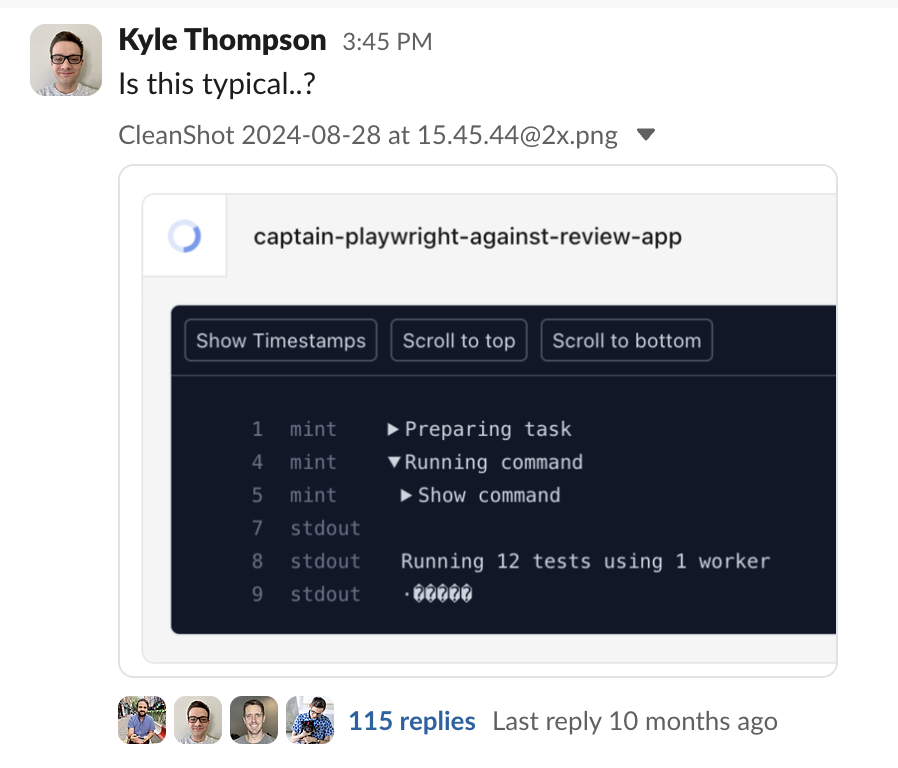
#Node 22.7 Buffer Issues
Earlier that day, we had upgraded from Node 22.6.0 to Node 22.7.0. It turns out, that version of Node introduced several encoding issues.
Hi! v22.7.0 has a few known buffer issues
#Minor Versions Matter
Minor versions of runtimes can introduce bugs. We've also previously run into an issue due to an inconsistency in a patch version.
As a best practice, ensure a consistent version is used across all environments. Especially be sure to test against the version that you'll use in production. Pin to a specific version rather than "22.x"
#Tool Versions
.tool-versions is a common file used for configuring dependencies.
It works with asdf, mise, other runtime version managers.
nodejs 22.17.0
You can easily use the .tool-versions file in your RWX workflows with the rwx/tool-versions package.
tasks:- key: codecall: git/clone 1.6.7with:repository: ...- key: tool-versionsuse: codecall: rwx/tool-versions 1.0.4filter: [.tool-versions]- key: nodecall: nodejs/install 1.1.7with:node-version: ${{ tasks.tool-versions.values.nodejs }}
Related posts

What would GitHub Actions look like if you designed it today?
GHA was designed in ~2018. What would it look like if you designed it today, with all we know now?
Truly continuous integration: ensuring pull requests from agents have passing builds
RWX CLI v3.0.0 introduces new tools for developers and coding agents to iterate on changes until CI passes - without a single commit or push.